Project
Security and Privacy Experiences (SPEX)
Project URL
Contact: cfaklai@charlotte.edu
The Security and Privacy Experiences (SPEX) research group focuses on people as risk navigators within a web of social relationships, systems, and computation-in-the-loop. We seek to (1) better understand people’s lived experiences of security and privacy, and (2) empower computing users to keep themselves and their loved ones safe. To do this, we draw on methods from human-computer interaction, design, software engineering, data science + applied statistics, and social psychology. SPEX has active projects in three research areas: (a) empirical research, (b) everyday interventions, and (c) adoption strategies. For the first area, we are gathering data on people’s mental models around phishing and ransomware attacks carried out through mobile messaging, and we are developing new interface designs and training to mitigate such attacks (with a focus on the banking sector and on distributed energy infrastructure). For the second area, we are developing a human-AI advice program and a cybersecurity “fitness” tracker, both for use by the public. For the third area, we are devising metrics and frameworks that pull together in one place what we know about how to motivate – and measure – behavior change for security and privacy.
Autonomous Cyber Deception
Project URL: Active-Cyber-Defense
Contact: jwei8@uncc.edu, ehab@cmu.edu
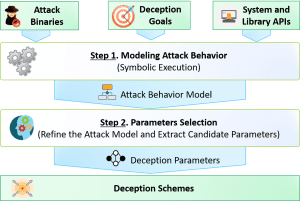
Malware attacks have evolved to be highly evasive against prevention and detection techniques. A significant number of new malware samples are launched each day and many of them remain undetected for a long period (e.g., more than five months). Cyber deception has emerged as an effective and complementary defense technique that proactively increases cyber resistance and deterrence. Approaches in this domain deliberately introduce misinformation or misleading functionality into cyberspace in order to trick adversaries in ways that render attacks ineffective or infeasible. We develop a novel approach that can construct deception plans against malware on the fly based on automated analysis of the malware’s behavior. More specifically, our approach (1) employs deception-oriented malware symbolic execution analysis that is capable of extracting deception parameters that are reconfigurable or misrepresentable in the cyber environment, yet the malware depends on to achieve its goals, (2) dynamically constructs the most cost-effective and scalable deception ploy that manipulates the deception parameters to achieve deception goals, and (3) translates and orchestrates the deception ploys into configuration actions to construct a run-time malware deception environment.
Defense against Kernel Queue Injection Malware
Project URL: kqueue.html
Contact: jwei8@uncc.edu
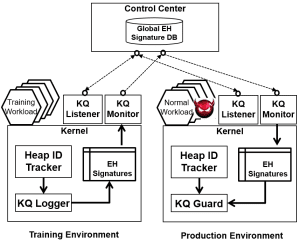
Kernel callback queues (KQs) are the established mechanism for event handling in modern kernels. Unfortunately, real-world malware has abused KQs to run malicious logic, through an attack called kernel queue injection (KQI). Current kernel-level defense mechanisms have difficulties with KQI attacks, since they work without necessarily changing legitimate kernel code or data. In this project, we design, implement, and evaluate KQguard, an efficient and effective protection mechanism of KQs. KQguard employs static and dynamic analysis of kernel and device drivers to learn specifications of legitimate event handlers. At runtime, KQguard rejects all the unknown KQ requests that cannot be validated. We implement KQguard on the Windows Research Kernel (WRK), Windows XP, and Linux, using source code instrumentation or binary patching. Our extensive experimental evaluation shows that KQguard is effective (i.e., it can have zero false positives against representative benign workloads after enough training and very low false negatives against 125 real-world malware), and it incurs a small overhead (up to ~5%). We also present the result of an automated analysis of 1,528 real-world kernel-level malware samples aiming to detect their KQ Injection behaviors. KQguard protects KQs in both Windows and Linux kernels, can accommodate new device drivers, and can support closed source device drivers through dynamic analysis of their binary code.
Online misinformation
Project URL
Contact: lzhou8@charlotte.edu
Online deception and misinformation have been fueled by the deep penetration of the Internet and social media in support of personal and business communications. The identification of indicators and signals of deception or misinformation is instrumental to the detection task. We have investigated multiple dimensions of indicators of online deception, including lexical, structural, and discourse behaviors, in a variety of settings. In addition, we have developed and enhanced a variety of traditional machine learning and deep learning models for automatic deception detection and for augmentation of human detection.
Ethical Guidelines and Privacy Protections for Health Data Using Blockchain Technology
Contact: cbrown@uncc.edu
Examines the role of ethical frameworks and level of privacy protections in building trust for genomic and other health data using blockchain technology.
Automating cyber defense leveraging Large Language Models
Contact: billchu@uncc.edu
This project focuses on extracting actionable cyber intelligence from a variety of real-time sources, such as social media feeds and online forums to continuously monitoring, analyzing, and interpreting vast amounts of data to identify potential cyber threats and vulnerabilities.We explore the application of advanced natural language processing (NLP) techniques, inherent in LLMs, to comprehend and process unstructured data. A significant component of the project is the development of an automated response mechanism. This mechanism will use the insights gained from the LLMs to formulate and implement timely and effective mitigation strategies against identified threats. The system will be designed to dynamically adapt its defense mechanisms in response to the evolving nature of cyber threats.
Hands-on Learning Experiences for Cyber Threat Hunting Education
Project URL: cyberthreathunting
Contact: jwei8@uncc.edu, billchu@uncc.edu, mshehab@uncc.edu
Cyber threat hunting has emerged as a critical part of cyber security practice. However, there is a severe shortage of cybersecurity professionals with advanced analysis skills for cyber threat hunting. More specifically, automation using Artificial Intelligence is reducing the need for human intervention in cyber defense, at the same time, it has increased the demand for cybersecurity professionals with more advanced analysis skills. As corroborated by a recent survey of IT professionals by SANS Institute, cyber threat hunting is an example of advanced analysis skills in great demand. We are developing freely-available, hands-on learning materials for cyber threat hunting suitable for use in two-year community college curriculum, 4-year universities curriculum, as well as for collegiate threat hunting competitions. The objectives of this project are: (1) develop hands-on learning experiences that cover two important areas in threat hunting: threat analysis and security data analytics, and (2) build institutional capacity by integrating hands-on labs on threat hunting into existing curricula at two participating institutions: UNC Charlotte and Forsyth Tech.
Implicit One-handed Mobile User Authentication by Induced Thumb Biometrics on Touch-screen Handheld Devices
Project URL: https://canshot.github.io/kaim2/MUA/
Contact: lzhou8@uncc.edu
The objective of this project is to improve both security and usability of mobile user authentication. The project will support one-handed mobile authentication on a touch-screen mobile device by inducing thumb biometrics and by enabling one-handed text entry based on thumb strokes.
Securing American Manufacturing
Project URL
Contact: AidanBrowne@uncc.edu
The Securing American Manufacturing (SAM) project is sponsored by the Office of the Secretary of Defense Manufacturing Technology Program (ManTech) and the Department of Energy Advanced Manufacturing Office (AMO). SAM addresses the intensifying concern expressed by the President; Congress; the Department of Defense Under Secretary of Defense for Acquisition, Technology, and Logistics; and the Deputy Assistant Secretary of Defense for Manufacturing Industrial Base Policy over the cybersecurity of networked manufacturing systems – the information supply chain, with emphasis on determining the effectiveness of the Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012, “Safeguarding of Unclassified Controlled Technical Information (CTI),” on the small to medium size manufacturing companies that are the backbone of the defense industrial base (DIB).